Overview
Finding the right policies for IT risk, compliance and security is a balancing act between the business' need for agility and continuity, compliance with regulations, and the cost and effort of implementing risk mitigation actions. Not achieving the right balance could result in lost revenues, legal issues or major incidents with unknown consequences. You don’t want to gamble with your IT. Unfortunately, many organizations are doing just that due to lack of transparency over the IT landscape and insufficient tools for effective risk and compliance assessments. Help is here: Leading international companies are using strategic portfolio management (SPM) and enterprise architecture (EA) capabilities to ensure IT risk managers can fulfill their responsibilities and reduce IT risks. Interested in knowing how to play it safe?
The challenges of tackling IT risk, security and compliance
IT risk managers cannot tackle IT risk, security and compliance if IT is not transparent. Essential to the task is the knowledge of what applications you have, who is using them, for what purpose, and on what information and infrastructure they depend. Without this transparency, you cannot take the next step—organizing assessments, prioritizing risks, and implementing controls. However, several challenges need to be overcome first to get IT risk, security and compliance under control.
Do you have an inventory of the IT and how it supports the business?
Does this inventory cover different levels, such as processes, applications and information objects, and the relationships between these? This inventory needs to be proactively managed and kept up-to-date. If not, you will not be able to manage IT risk.
Are there assessments in place for risks and IT controls?
Assessments need to be automated to minimize the manual effort in sending, checking, tracking and consolidating self-assessment questionnaires. Without automation, you spend more money on assessments than necessary and risk manual errors, wasting IT operations spending.
Is there a risk-aware IT planning process in place?
The IT planning process must ensure that IT solutions being developed comply with IT security policy. Risk assessments need to be done for new and impacted applications as part of the approval process. If not, changes to your IT landscape increase risk.
Can you see risk from a business perspective?
You need the ability to take the results of risk assessments and aggregate and abstract them in business terms to see the risk to a process, capability or organizational unit. If not, you cannot discuss trade-offs between accepting and mitigating risks in business terms.
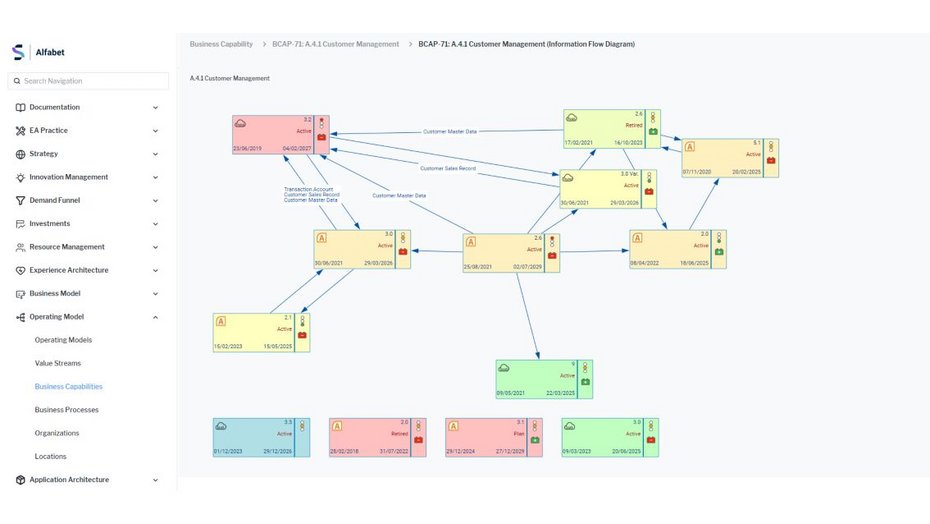
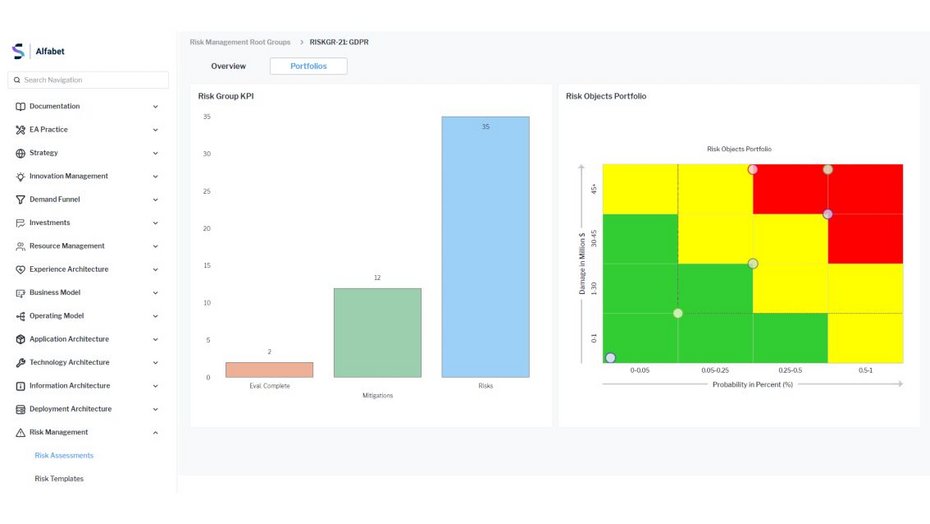
Find the answers with SPM and EA
With SPM and EA, best-in-class IT risk managers implement the necessary processes and governance into IT risk and compliance management. By doing so, they support different stakeholders with core capabilities to meet the challenges of tackling IT risk, security and compliance:
- Do you understand the IT landscape and how it supports business?
- Are your risk and IT control assessments efficient?
- Does the IT governance in place ensure that the IT security policy is adhered to?
These key questions are answered by the following essential capabilities.
IT risk management
IT risk management allows you to assess IT risks for your applications, projects, data and other parts of the IT landscape, including the analysis and prioritization of mitigation steps. Assessments are automated with workflows, drastically reducing manual effort. You can define the necessary IT controls to mitigate risk and fulfill regulatory and corporate compliance obligations.
IT planning
IT planning converts business demand into executable and funded IT programs. It enables target architectures and scenarios to be iterated with the business and broken down into roll-out plans and project milestones. It also implements appropriate planning and approval processes to ensure any new applications or changes to existing ones do not increase your IT risk or conflict with IT security policy.
Enterprise architecture management
Enterprise architecture management provides the foundation for IT risk management—the IT scope. It has a model of how processes, applications, information, etc. are related and maintains an inventory of these objects and their relationships. Furthermore, it supports the abstraction and aggregation of risk and other indicators to enable you to express issues in business terms: process, organization, capability.
Process-based platform
Standard reports, software and methodology are available out-of-the box to kickstart IT risk and compliance management programs. The workflow engine and role-based access support the necessary processes, such as assessments and approvals, while giving stakeholders the view of IT risk, compliance and security issues that they need.
Leader in SPM and EA
Internationally renowned companies across the globe use the market-leading solution for SPM and EA—Alfabet. The platform provides a set of core capabilities to sustainably manage and ensure IT’s contribution to business value. SPM and EA aim to plan and monitor the performance of IT support throughout its entire life cycle—ensuring that business strategy and demands are fully understood, prioritized and executed, and that the costs, quality and risks to IT support are known and considered during decision making.
We respond to potential crises a lot faster. Once we know everything about a zero-day exploit, we turn to Alfabet to identify, on time, the right managers to involve and all the impacted assets.
About Alfabet
Alfabet is a leading enterprise platform with standard modules that support effective Strategic Portfolio Management (SPM) and EA, offering:
- The richest set of artifacts in the industry
- A single, central repository
- Role-based access and support for global communities
- Decision-ready reporting and publication
- Advanced support for the agile enterprise
- Broad and easy-to-use configuration
- Use of leading-edge AI technologies
- Support for federated enterprises



